Expected Corteza to handle data encryption automatically and not store any sensitive data as plain text once sensitivity levels at module & record fields along with “Data at rest protection provided in Connections” are enabled.
Did I miss a critical step?
Setup & database sample where data is stored as plain text in database:
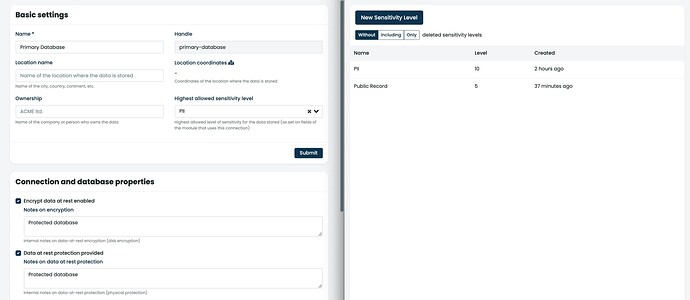
- System → Connections → Primary Connection
- System → Sensitivity Levels → PII
dal_sensitivity_levels
INSERT INTO public.dal_sensitivity_levels (id, handle, level, meta) VALUES (417852788414676993, ‘pii’, 10, ‘{“name”: “PII”, “description”: “For all PII data”}’);
compose_module_field
INSERT INTO public.compose_module_field (name, label, config) VALUES (‘phone’, ‘Phone number’, ‘{“dal”: {“encodingStrategy”: null}, “privacy”: {“usageDisclosure”: “Customers phone number is PII data”, “sensitivityLevelID”: “417852788414676993”}, “recordRevisions”: {“enabled”: false}}’);
compose_module
INSERT INTO public.compose_module (handle, name, meta, config) VALUES (‘customers’, ‘Customers’, ‘{}’, ‘{“dal”: {“ident”: “”, “constraints”: null, “connectionID”: “417852788131823617”, “systemFieldEncoding”: {“id”: null, “meta”: null, “ownedBy”: null, “moduleID”: null, “revision”: null, “createdAt”: null, “createdBy”: null, “deletedAt”: null, “deletedBy”: null, “updatedAt”: null, “updatedBy”: null, “namespaceID”: null}}, “privacy”: {“usageDisclosure”: “PII of customers”, “sensitivityLevelID”: “417852788414676993”}, “discovery”: {“public”: {“result”: [{“lang”: “”, “fields”: []}]}, “private”: {“result”: [{“lang”: “”, “fields”: []}]}, “protected”: {“result”: [{“lang”: “”, “fields”: []}]}}, “recordDeDup”: {}, “recordRevisions”: {“ident”: “”, “enabled”: false}}’);
compose_record
INSERT INTO public.compose_record (rel_module, values) VALUES (417852788433289217, ‘{“name”: [“John Doe”], “phone”: [“1234567890”], “linkedin”: [“https://www.linkedin.com/john-doe”]}’);